Codetown
Codetown ::: a software developer's community
-
Paul Stearns
- Male
- Share on Facebook MySpace Tweet
- Blog Posts
- Discussions (16)
- Events
- Groups (2)
- Photos
- Photo Albums
- Videos
Paul Stearns's Discussions
Another question on refactoring my NetBeans generated GUI code
Hello all:It has been a few months since my last question. Had a lot of other projects taking up my time, but I am back to fighting with my Planetarium lighting controller. I have it working, but I…Continue
Started Jun 20, 2012
Creating separate class files in a large project
9 Replies
Hello all:I have been working on a GUI interface for controlling lights in a planetarium. I had some trouble getting the communication to happen, and received some help from this forum to get past…Continue
Started this discussion. Last reply by Jackie Gleason Feb 10, 2012.
Sending strings between two computers via ethernet
13 Replies
A while ago I asked a question about using RS-232 communication with Java. It seems as though I need to abandon that route because it no longer fits the desired system requirements. Thanks to Nem…Continue
Started this discussion. Last reply by Paul Stearns Oct 5, 2011.
Using rs-232 in a java desktop application
4 Replies
Hello all: I am fairly new to the Java world and would like some advice on how to handle rs-232 communications with a Java based GUI I am working on. Several years ago I created a similar GUI with…Continue
Tags: communication, rs-232, using, application, Java
Started this discussion. Last reply by Nemanja Nesic - NEM- Jun 9, 2011.
Gifts Received

Paul Stearns has not received any gifts yet
Paul Stearns's Page
Profile Information
- How did you hear about Codetown?
- Janet Gatsby
- What are your main interests in software development?
- Want to better understand what Java can do.
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
Netflix Automates RDS PostgreSQL to Aurora PostgreSQL Migration Across 400 Production Clusters
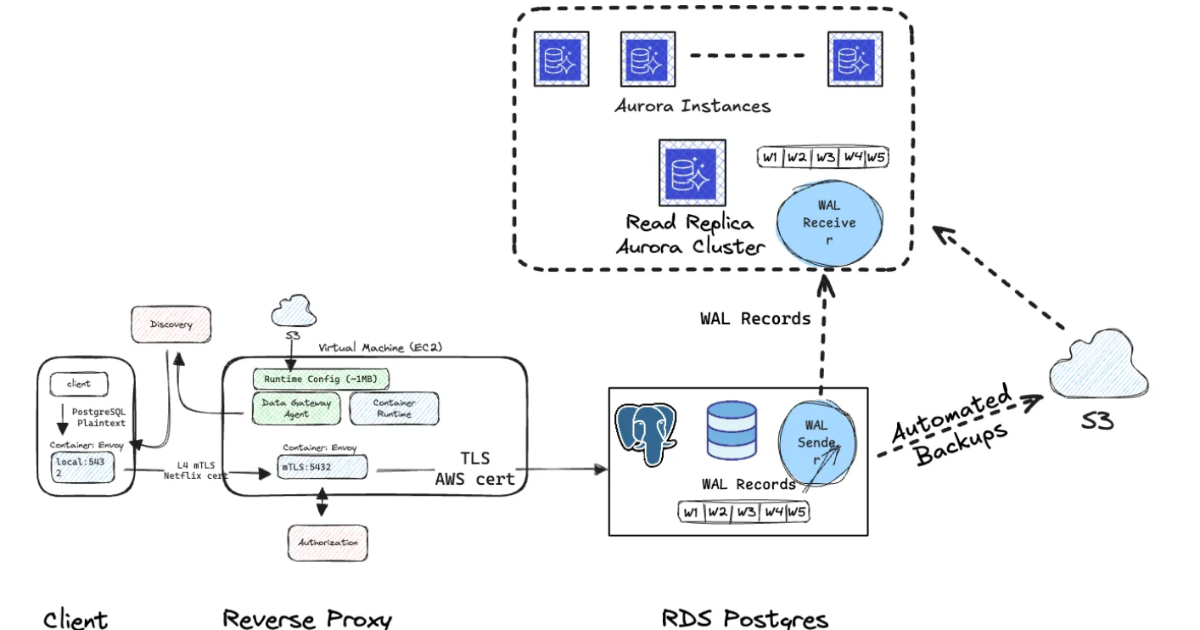
Netflix engineers describe an internal automation platform that migrates nearly 400 RDS PostgreSQL clusters to Aurora, reducing downtime and operational risk. The platform coordinates replication, CDC handling, controlled cutover, and rollback, while supporting service teams in a self-service migration workflow.
By Leela KumiliPresentation: 4 Patterns of AI Native Development

Patrick Debois discusses the evolution of software engineering in the age of AI. He shares four key patterns: transitioning from producer to manager, focusing on intent over implementation through spec-driven development, moving from delivery to discovery, and managing agentic knowledge. He explains how these shifts redefine seniority, team roles, and the future of the DevOps workflow.
By Patrick DeboisJava News Roundup: Apache Solr 10, LangChain4j, Grails, JobRunr, Gradle, Devnexus, Commonhaus

This week's Java roundup for March 2nd, 2026, features news highlighting: the GA release of Apache Solr 10; point releases of LangChain4j, JobRunr, Multik and Gradle; maintenance releases of Grails and Keycloak; Devnexus 2026; and Pi4J joining the Commonhaus Foundation.
By Michael RedlichPodcast: Mindful Leadership in the Age of AI

In this episode, Thomas Betts and Sam McAfee discuss how AI hype is reshaping organizational behavior, why many companies struggle with experimentation, and how unclear decision structures create friction. They explore psychological safety and mindful leadership as essential foundations for healthier, more effective engineering cultures.
By Sam McAfeeArticle: Change as Metrics: Measuring System Reliability Through Change Delivery Signals
System changes are the primary driver of production incidents, making change-related metrics essential reliability signals. A minimal metric set of Change Lead Time, Change Success Rate, and Incident Leakage Rate assesses delivery efficiency and reliability, supported by actionable technical metrics and an event-centric data warehouse for unified change observability.
By Peihao Yuan
© 2026 Created by Michael Levin.
Powered by
![]()
Comment Wall (1 comment)
You need to be a member of Codetown to add comments!
Join Codetown