Codetown
Codetown ::: a software developer's community
The Future of GWT Report
This report on GWT, "The Future of GWT", will be interesting to developers, architects and managers, too. You'll learn details about GWT's usability, its competitors and even opinions as to how it's going to stand up against Dart.
Over 1300 respondents provided data. Overall, GWT is looked upon highly by developers mainly because it targets multiple browsers at once and because it reduces hand coding of Javascript. Slow compile times were a major complaint. These comments are pretty obvious to anyone familiar with GWT, but useful to newcomers. The report digs much deeper though, so experienced developers will learn some things by seeing what a good size survey respondent sample thinks.
Here's a preview of what you'll see in the report:
You'll have to provide your name and email address to get a copy, but I think it's fair since the folks at Vaadin worked hard to provide it along with the other big contributors. And, thanks to Dave Booth for bringing this info to Codetown. If you have questions, Dave's your direct link to the group that put the report together. Check it out here.
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
Cloudflare Releases Experimental Next.js Alternative Built With AI Assistance

Cloudflare released vinext, an experimental Next.js reimplementation built on Vite by one engineer, with AI guidance over one week, for $1,100. Early benchmarks show 4.4x faster builds, but Cloudflare cautions it's untested at scale. Missing static pre-rendering. HN reaction skeptical, noting Vite does the heavy lifting. Already running on CIO.gov despite experimental status.
By Steef-Jan WiggersNetflix Automates RDS PostgreSQL to Aurora PostgreSQL Migration Across 400 Production Clusters
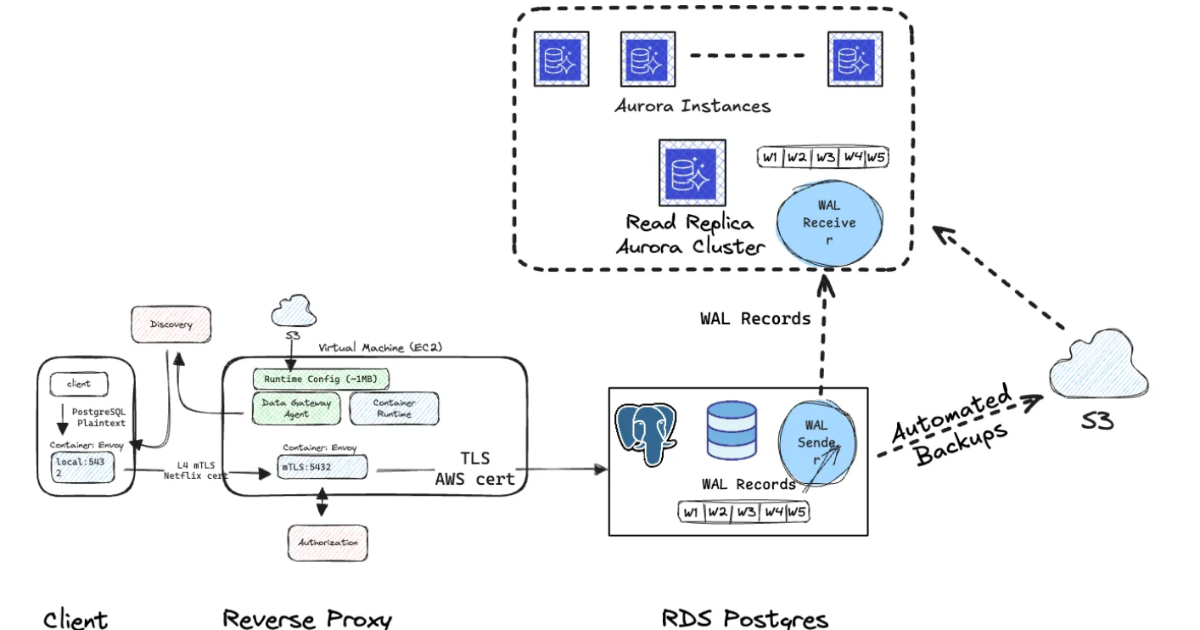
Netflix engineers describe an internal automation platform that migrates nearly 400 RDS PostgreSQL clusters to Aurora, reducing downtime and operational risk. The platform coordinates replication, CDC handling, controlled cutover, and rollback, while supporting service teams in a self-service migration workflow.
By Leela KumiliPresentation: 4 Patterns of AI Native Development

Patrick Debois discusses the evolution of software engineering in the age of AI. He shares four key patterns: transitioning from producer to manager, focusing on intent over implementation through spec-driven development, moving from delivery to discovery, and managing agentic knowledge. He explains how these shifts redefine seniority, team roles, and the future of the DevOps workflow.
By Patrick DeboisJava News Roundup: Apache Solr 10, LangChain4j, Grails, JobRunr, Gradle, Devnexus, Commonhaus

This week's Java roundup for March 2nd, 2026, features news highlighting: the GA release of Apache Solr 10; point releases of LangChain4j, JobRunr, Multik and Gradle; maintenance releases of Grails and Keycloak; Devnexus 2026; and Pi4J joining the Commonhaus Foundation.
By Michael RedlichPodcast: Mindful Leadership in the Age of AI

In this episode, Thomas Betts and Sam McAfee discuss how AI hype is reshaping organizational behavior, why many companies struggle with experimentation, and how unclear decision structures create friction. They explore psychological safety and mindful leadership as essential foundations for healthier, more effective engineering cultures.
By Sam McAfee
© 2026 Created by Michael Levin.
Powered by
![]()
You need to be a member of Codetown to add comments!
Join Codetown