Codetown
Codetown ::: a software developer's community
Kotlin Thursdays - Introduction to Functional Programming Part 2
Resources
- Higher-Order Functions and Lambdas:https://kotlinlang.org/docs/reference/lambdas.html
- FP in Kotlin Part 1: https://medium.com/kotlin-thursdays/functional-programming-in-kotli...
Introduction
Last week, we went over higher order functions in Kotlin. We learned how higher order functions can accept functions as parameters and are also able to return functions. This week, we will take a look at lambdas. Lambdas are another type of function and they are very popular in the functional programming world.
Logic & Data
Computer programs are made up of two parts: logic and data. Usually, logic is described in functions and data is passed to those functions. The functions do things with the data, and return a result. When we write a function we would typically create a named function. As we saw last week, this is a typical named function:
fun hello(name: String): String {
return "Hello, $name"
}
Then you can call this function:
fun main() {
println(hello("Matt"))
}
Which gives us the result:
Hello, Matt
Functions as Data
There is a concept in the functional programming world where functions are treated as data. Lambdas (functions as data) can do the same thing as named functions, but with lambdas, the content of a given function can be passed directly into other functions. A lambda can also be assigned to a variable as though it were just a value.
Lambda Syntax
Lambdas are similar to named functions but lambdas do not have a name and the lambda syntax looks a little different. Whereas a function in Kotlin would look like this:
fun hello() {
return "Hello World"
}
The lambda expression would look like this:
{ "Hello World" }
Here is an example with a parameter:
fun(name: String) {
return "Hello, ${name}"
}
The lambda version:
{ name: String -> "Hello, $name" }
You can call the lambda by passing the parameter to it in parentheses after the last curly brace:
{ name: String -> "Hello, $name" }("Matt")
It’s also possible to assign a lambda to a variable:
val hello = { name: String -> "Hello, $name" }
You can then call the variable the lambda has been assigned to, just as if it was a named function:
hello("Matt")
Lambdas provide us with a convenient way to pass logic into other functions without having to define that logic in a named function. This is very useful when processing lists or arrays of data. We’ll take a look at processing lists with lambdas in the next post!
Tags:
Replies to This Discussion
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
Scaling Human Judgment: How Dropbox Uses LLMs to Improve Labeling for RAG Systems
To improve the relevance of responses produced by Dropbox Dash, Dropbox engineers began using LLMs to augment human labelling, which plays a crucial role in identifying the documents that should be used to generate the responses. Their approach offers useful insights for any system built on retrieval-augmented generation (RAG).
By Sergio De SimoneAWS Introduces Nested Virtualization on EC2 Instances

AWS recently announced support for nested virtual machines within virtualized EC2 instances running KVM or Hyper-V. A long-awaited feature by the community, the new option enables use cases such as app emulation and hardware simulation on supported C8i, M8i, and R8i instances.
By Renato LosioStandardizing Post-Quantum IPsec: Cloudflare Adopts Hybrid ML-KEM to Replace Ciphersuite Bloat

Cloudflare has extended hybrid post-quantum encryption to IPsec and WAN traffic, standardizing its SASE stack ahead of the NIST 2030 deadline. By adopting a streamlined ML-KEM key exchange, the move addresses long-standing "ciphersuite bloat" in quantum-resistant IPsec. The update aims to neutralize "harvest now, decrypt later" threats without requiring specialized hardware upgrades.
By Steef-Jan WiggersNew Research Reassesses the Value of AGENTS.md Files for AI Coding

Despite widespread industry recommendations, a new ETH Zurich paper concludes that AGENTS.md files may often hinder AI coding agents. The researchers recommend omitting LLM-generated context files entirely and limiting human-written instructions to non-inferable details, such as highly specific tooling or custom build commands.
By Bruno CouriolArchitecting for Global Scale: Inside DoorDash’s Unified, Composable Dasher Onboarding Platform
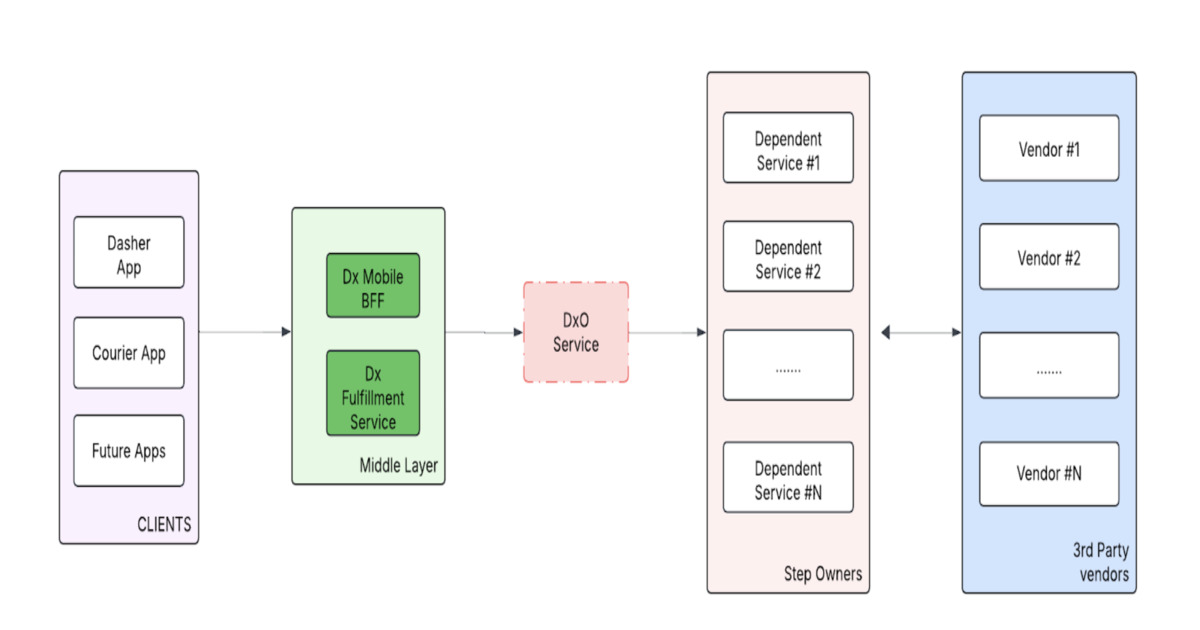
DoorDash has rebuilt its Dasher onboarding into a unified, modular platform to support global expansion. The new architecture uses reusable step modules, a centralized status map, and workflow orchestration to ensure consistent, localized onboarding experiences. This design reduces complexity, supports market-specific variations, and enables faster rollout to new countries.
By Leela Kumili
© 2026 Created by Michael Levin.
Powered by
![]()