Codetown
Codetown ::: a software developer's community
Are you interested in learning about graph databases? The folks at Neo4J published a book and it's free! Here's a link to the download page: http://graphdatabases.com/
Tags:
Replies to This Discussion
-
Permalink Reply by Juan Rolando Reza on March 16, 2015 at 4:45pm
-
Database representation of graph-structured information is fascinating in its own right.
I have been studying genomics technology in which graphs play a big role, both as information-structure that is the basis of certain algorithms, as well as the data driving visualizations or visually-interesting real-world structures.
As an example, here is a visualization of a protein complex that catches the eye.
See http://en.wikipedia.org/wiki/FOXP2#/media/File:Protein_FOXP2_PDB_2a...
The image is a Richardson diagram which is (mostly) automatically generated from a database describing the molecular structure of the protein. This type of diagram was invented (i.e. originally hand-drawn) by Jane Richardson, PhD.
I wonder if the book "Graph Databases" touches on this.
Presently, I am doing a research study on a particular feature of the epigenome. It involves large DNA databases (actually, structured flat files), elaborate algorithms for sequence correlation, and histone complexes. Each of these involves graph-theoretic representations and inference functions from graph structures.
The "databases" I know for DNA, the transcriptome, pathways, etc. do not lend themselves to conventional SQL, or even noSQL as far as I know to date. (Chime in anyone? )
I will be presenting a paper at the IEEE SouthCon conference in April 2015 which touches on a graph-theoretic feature of certain (sequencing) problems lending itself to massively-parallel-ization of linearly-expressable algorithms.
I am pleased to see a free book on graph databases. Thanks!
-
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
Scaling Human Judgment: How Dropbox Uses LLMs to Improve Labeling for RAG Systems
To improve the relevance of responses produced by Dropbox Dash, Dropbox engineers began using LLMs to augment human labelling, which plays a crucial role in identifying the documents that should be used to generate the responses. Their approach offers useful insights for any system built on retrieval-augmented generation (RAG).
By Sergio De SimoneAWS Introduces Nested Virtualization on EC2 Instances

AWS recently announced support for nested virtual machines within virtualized EC2 instances running KVM or Hyper-V. A long-awaited feature by the community, the new option enables use cases such as app emulation and hardware simulation on supported C8i, M8i, and R8i instances.
By Renato LosioStandardizing Post-Quantum IPsec: Cloudflare Adopts Hybrid ML-KEM to Replace Ciphersuite Bloat

Cloudflare has extended hybrid post-quantum encryption to IPsec and WAN traffic, standardizing its SASE stack ahead of the NIST 2030 deadline. By adopting a streamlined ML-KEM key exchange, the move addresses long-standing "ciphersuite bloat" in quantum-resistant IPsec. The update aims to neutralize "harvest now, decrypt later" threats without requiring specialized hardware upgrades.
By Steef-Jan WiggersNew Research Reassesses the Value of AGENTS.md Files for AI Coding

Despite widespread industry recommendations, a new ETH Zurich paper concludes that AGENTS.md files may often hinder AI coding agents. The researchers recommend omitting LLM-generated context files entirely and limiting human-written instructions to non-inferable details, such as highly specific tooling or custom build commands.
By Bruno CouriolArchitecting for Global Scale: Inside DoorDash’s Unified, Composable Dasher Onboarding Platform
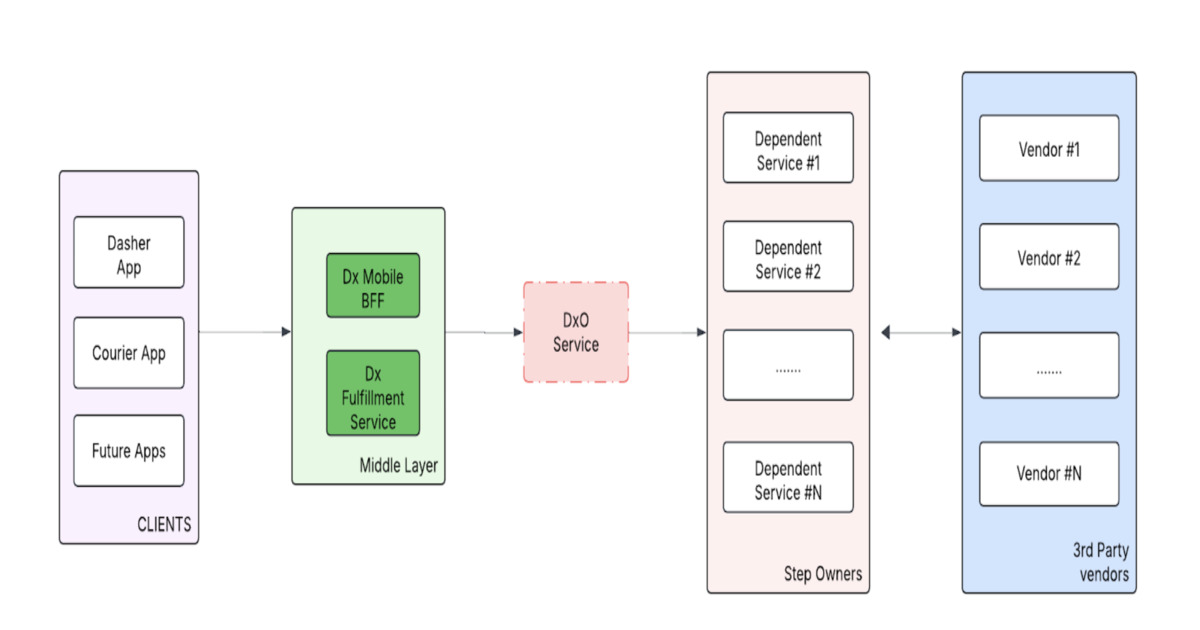
DoorDash has rebuilt its Dasher onboarding into a unified, modular platform to support global expansion. The new architecture uses reusable step modules, a centralized status map, and workflow orchestration to ensure consistent, localized onboarding experiences. This design reduces complexity, supports market-specific variations, and enables faster rollout to new countries.
By Leela Kumili
© 2026 Created by Michael Levin.
Powered by
![]()