Codetown
Codetown ::: a software developer's community
Java (36)
Sort by:
| Discussions | Replies | Latest Activity |
|---|---|---|
How To Compile Multiple Files Using NetBeans 6.5Hello, I'm new to Java and have been using NetBeans 6.5 as my IDE. I have been learning how to create classes and have come to the point w… Started by Mark Hollinger |
0 | Aug 12, 2009 |
Facebook connect JSThis is more javascript. However, I have been playing around with facebook connect on a website I am coding for and it is kind of a cool fe… Started by Tim Stevesi |
2 |
Jun 18, 2009 Reply by Tim Stevesi |
Courses translated to frenchI want courses of iphone's development in french. Started by Mara |
2 |
May 27, 2009 Reply by Michael Levin |
Comparing Tomcat and GlassfishThere is a direct connection between the Web container technology used by developers and the performance and agility of applications. This… Started by Carol McDonald |
0 | Mar 6, 2009 |
JavaFXhttp://weblogs.java.net/blog/caroljmcdonald/archive/2008/12/javafx_restful.html JavaFX RESTful Pet Catalog Client: a JavaFX application th… Started by Carol McDonald |
1 |
Dec 7, 2008 Reply by Michael Levin |
OJUG Mule Demo Source CodeHi All, What a great night! To those who are interested for the presentation slides and source code of my demo, you may download it here:… Started by Zemian Deng |
0 | Nov 20, 2008 |
- ‹ Previous
- 1
- 2
- 3
- 4
- Next ›
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
Netflix Automates RDS PostgreSQL to Aurora PostgreSQL Migration Across 400 Production Clusters
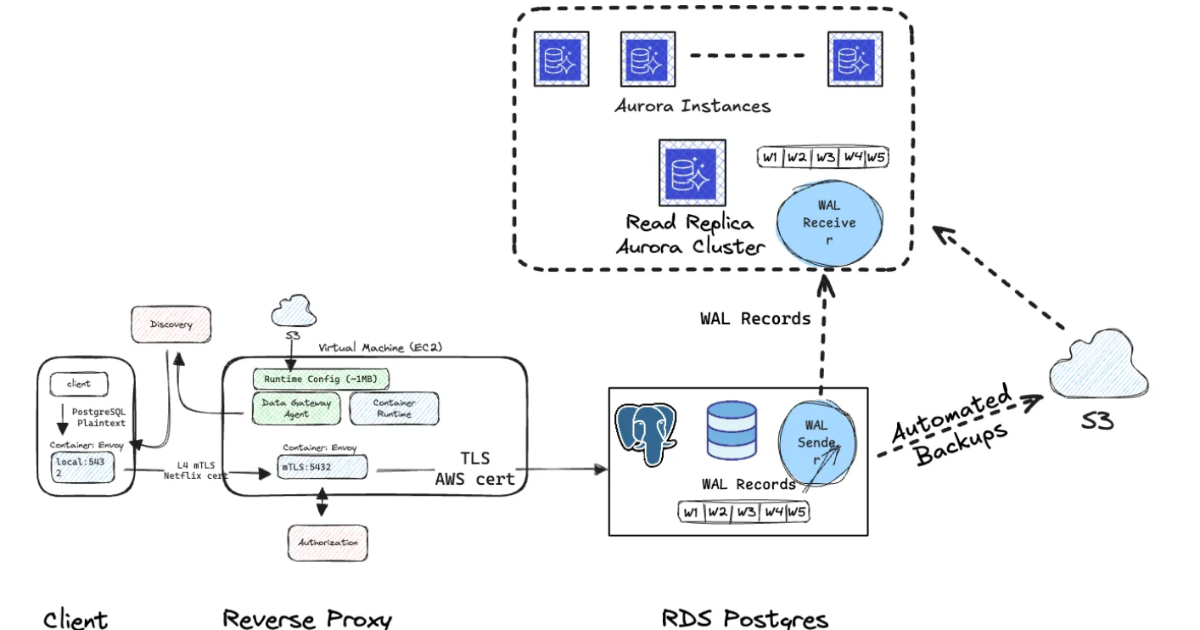
Netflix engineers describe an internal automation platform that migrates nearly 400 RDS PostgreSQL clusters to Aurora, reducing downtime and operational risk. The platform coordinates replication, CDC handling, controlled cutover, and rollback, while supporting service teams in a self-service migration workflow.
By Leela KumiliPresentation: 4 Patterns of AI Native Development

Patrick Debois discusses the evolution of software engineering in the age of AI. He shares four key patterns: transitioning from producer to manager, focusing on intent over implementation through spec-driven development, moving from delivery to discovery, and managing agentic knowledge. He explains how these shifts redefine seniority, team roles, and the future of the DevOps workflow.
By Patrick DeboisJava News Roundup: Apache Solr 10, LangChain4j, Grails, JobRunr, Gradle, Devnexus, Commonhaus

This week's Java roundup for March 2nd, 2026, features news highlighting: the GA release of Apache Solr 10; point releases of LangChain4j, JobRunr, Multik and Gradle; maintenance releases of Grails and Keycloak; Devnexus 2026; and Pi4J joining the Commonhaus Foundation.
By Michael RedlichPodcast: Mindful Leadership in the Age of AI

In this episode, Thomas Betts and Sam McAfee discuss how AI hype is reshaping organizational behavior, why many companies struggle with experimentation, and how unclear decision structures create friction. They explore psychological safety and mindful leadership as essential foundations for healthier, more effective engineering cultures.
By Sam McAfeeArticle: Change as Metrics: Measuring System Reliability Through Change Delivery Signals
System changes are the primary driver of production incidents, making change-related metrics essential reliability signals. A minimal metric set of Change Lead Time, Change Success Rate, and Incident Leakage Rate assesses delivery efficiency and reliability, supported by actionable technical metrics and an event-centric data warehouse for unified change observability.
By Peihao Yuan
© 2026 Created by Michael Levin.
Powered by
![]()