Codetown
Codetown ::: a software developer's community
OSCON
Event Details
Time: May 16, 2016 to May 19, 2016
Location: Austin
City/Town: Austin
Website or Map: http://conferences.oreilly.co…
Event Type: conference
Organized By: Oreilly Media
Latest Activity: Dec 8, 2015
Event Description
Once considered a radical upstart, open source has moved from disruption to default. Its methods and culture commoditized the technologies that drove the Internet revolution and transformed the practice of software development. Collaborative and transparent, open source has become modus operandi, powering the next wave of innovation in cloud, data, and mobile technologies.
OSCON is where all of the pieces come together: developers, innovators, businesspeople, and investors. In the early days, this trailblazing O'Reilly event was focused on changing mainstream business thinking and practices; today OSCON is about real-world practices and how to successfully implement open source in your workflow or projects. While the open source community has always been viewed as building the future—that future is here, and it's everywhere you look. Since 1999, OSCON has been the best place on the planet to experience the open source ecosystem. At OSCON, you'll find everything open source: languages, communities, best practices, products and services. Rather than focus on a single language or aspect, such as cloud computing, OSCON allows you to learn about and practice the entire range of open source technologies.
In keeping with its O'Reilly heritage, OSCON is a unique gathering where participants find inspiration, confront new challenges, share their expertise, renew bonds to community, make significant connections, and find ways to give back to the open source movement. The event has also become one of the most important venues to announce groundbreaking open source projects and products.
"For those who have not been to OSCON, it's a great technical conference covering the whole spectrum of open source, including Linux, MySQL, the LAMP stack, Perl, Python, Ruby on Rails, middleware, applications, cloud computing, and more. OSCON always has great keynotes, tutorials, and evening Birds-of-a-Feather sessions. As with many conferences, a lot of the meat takes place in hallway conversations and impromptu sessions." —Zack Urlocker, InfoWorld
Experience OSCON
OSCON 2016 will educate, provoke, and inspire, with:
- Hundreds of sessions covering the full range of open source languages and platforms
- Practical tutorials that go deep into technical skills, new features and applications, and best practices
- Inspirational (and relevant) keynote presentations
- Over 4,000 open source developers, hackers, experts, vendors, and users of all levels—many of whom share your interests
- An Expo Hall packed with an impressive array of open source projects and products
- A vibrant "hallway track" where attendees, speakers, journalists, and vendors debate and discuss important issues
- Fun evening events and receptions, Birds of a Feather sessions, awards ceremonies, late night parties, OSCON activities around town, and plenty of networking opportunities for everyone
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
Netflix Automates RDS PostgreSQL to Aurora PostgreSQL Migration Across 400 Production Clusters
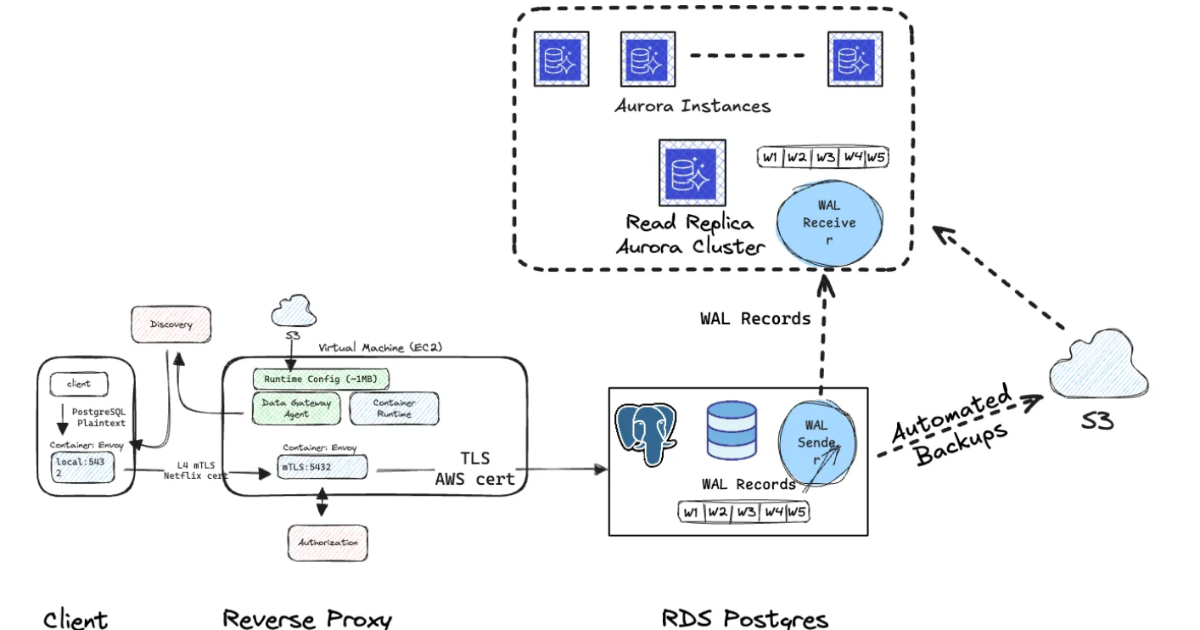
Netflix engineers describe an internal automation platform that migrates nearly 400 RDS PostgreSQL clusters to Aurora, reducing downtime and operational risk. The platform coordinates replication, CDC handling, controlled cutover, and rollback, while supporting service teams in a self-service migration workflow.
By Leela KumiliPresentation: 4 Patterns of AI Native Development

Patrick Debois discusses the evolution of software engineering in the age of AI. He shares four key patterns: transitioning from producer to manager, focusing on intent over implementation through spec-driven development, moving from delivery to discovery, and managing agentic knowledge. He explains how these shifts redefine seniority, team roles, and the future of the DevOps workflow.
By Patrick DeboisJava News Roundup: Apache Solr 10, LangChain4j, Grails, JobRunr, Gradle, Devnexus, Commonhaus

This week's Java roundup for March 2nd, 2026, features news highlighting: the GA release of Apache Solr 10; point releases of LangChain4j, JobRunr, Multik and Gradle; maintenance releases of Grails and Keycloak; Devnexus 2026; and Pi4J joining the Commonhaus Foundation.
By Michael RedlichPodcast: Mindful Leadership in the Age of AI

In this episode, Thomas Betts and Sam McAfee discuss how AI hype is reshaping organizational behavior, why many companies struggle with experimentation, and how unclear decision structures create friction. They explore psychological safety and mindful leadership as essential foundations for healthier, more effective engineering cultures.
By Sam McAfeeArticle: Change as Metrics: Measuring System Reliability Through Change Delivery Signals
System changes are the primary driver of production incidents, making change-related metrics essential reliability signals. A minimal metric set of Change Lead Time, Change Success Rate, and Incident Leakage Rate assesses delivery efficiency and reliability, supported by actionable technical metrics and an event-centric data warehouse for unified change observability.
By Peihao Yuan
© 2026 Created by Michael Levin.
Powered by
![]()
RSVP for OSCON to add comments!
Join Codetown