Codetown
Codetown ::: a software developer's community
Developer Day - Boulder, CO
Event Details
Time: October 10, 2009 all day
Location: Boulder
Street: 14th and Walnut St
City/Town: Boulder, CO 80302
Website or Map: http://developer-day.com/ and…
Phone: bscofield@developer-day.com
Event Type: conference
Organized By: Developers in Boulder!
Latest Activity: Oct 7, 2009
Event Description
Developer Day was born out of the realization that there's a huge amount of development talent and experience spread across the country, and there's absolutely no need to spend a lot of money to get together and learn from each other. Furthermore, so many of the venues for assembling geeks are focused on a single technology. We need less specialization right now, and more places to talk to people for whom tools are tools, but tech is king. When you want to talk to Ruby geeks, head out to RubyFringe or Ruby Hoedown. When Java is on top, catch an NFJS, or JavaOne. But where are you to go when you just want to talk to and hear from people who are putting a bunch of technologies to use solving interesting problems?
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
OpenAI Launches Prism, a Free LaTeX-Native Workspace with Integrated GPT-5.2

OpenAI has released Prism, a free, cloud-based LaTeX workspace designed for academic writing and collaboration, with GPT-5.2 integrated directly into the authoring environment. The platform combines document editing, compilation, citation management, and AI-assisted revision in a single web-based workspace, aimed at researchers producing long-form scientific documents.
By Robert KrzaczyńskiOpenEverest: Open Source Platform for Database Automation
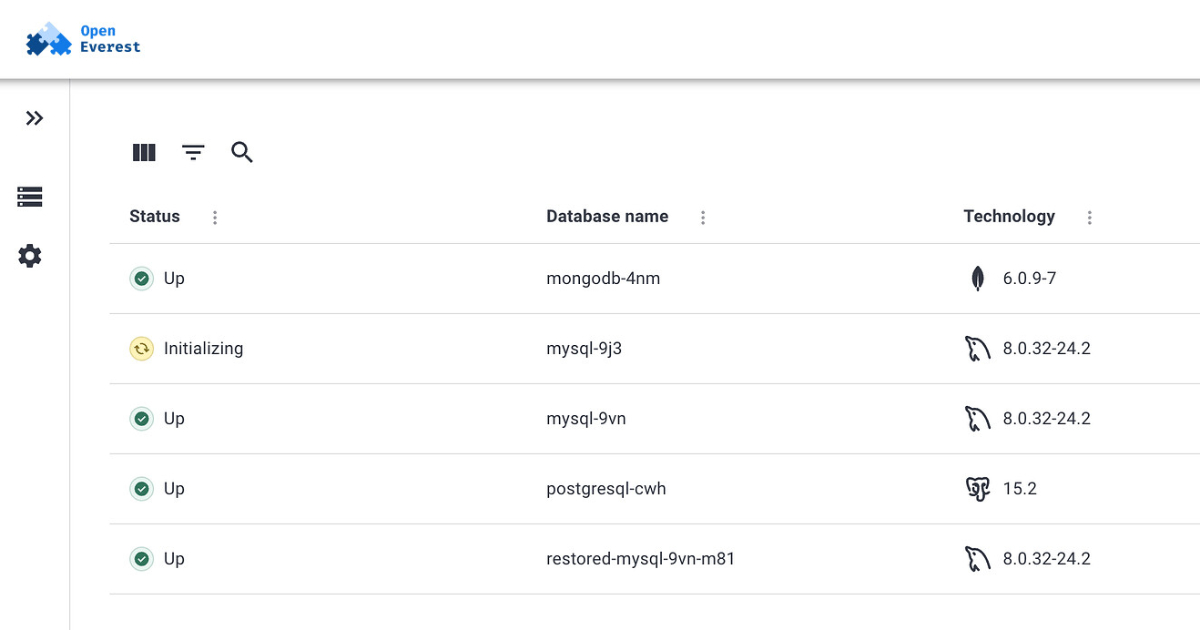
Percona recently announced OpenEverest, an open-source platform for automated database provisioning and management that supports multiple database technologies. Launched initially as Percona Everest, OpenEverest can be hosted on any Kubernetes infrastructure, in the cloud, or on-premises.
By Renato LosioGoogle Introduces Managed Connection Pooling for AlloyDB

Google Cloud has launched managed connection pooling for AlloyDB for PostgreSQL, boosting client connections by 3x and transactional throughput by up to 5x. This feature simplifies database management by automating connection management and reducing latency.
By Steef-Jan WiggersNVIDIA Dynamo Planner Brings SLO-Driven Automation to Multi-Node LLM Inference

Microsoft and NVIDIA have released Part 2 of their collaboration on running NVIDIA Dynamo for large language model inference on Azure Kubernetes Service (AKS). The first announcement aimed for a raw throughput of 1.2 million tokens per second on distributed GPU systems.
By Claudio MasoloMicrosoft Ships OData .NET (ODL) 9.0.0 Preview 3: Safety, Modern APIs, and Spec Compliance

Microsoft released OData .NET (ODL) 9.0.0 Preview 3, the latest preview iteration of the OData .NET client and core libraries, continuing the modernisation effort of the library. This preview focuses on safer default behaviours, runtime API cleanup, and closer conformance with the OData specification as the team works toward a stable 9.x release.
By Edin Kapić
© 2026 Created by Michael Levin.
Powered by
![]()
RSVP for Developer Day - Boulder, CO to add comments!
Join Codetown