Codetown
Codetown ::: a software developer's community
-
Tricia
- Female
- Share on Facebook MySpace Tweet
- Blog Posts
- Discussions
- Events
- Groups (1)
- Photos
- Photo Albums
- Videos
Tricia's Page
Gifts Received

Tricia has not received any gifts yet
Profile Information
- How did you hear about Codetown?
- Mike Levin
- What are your main interests in software development?
- Recruiting Software Development professionals
- Do you have a website?
- http://abtsolutions.com
Notes
Welcome to Codetown!
 Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Codetown is a social network. It's got blogs, forums, groups, personal pages and more! You might think of Codetown as a funky camper van with lots of compartments for your stuff and a great multimedia system, too! Best of all, Codetown has room for all of your friends.
Created by Michael Levin Dec 18, 2008 at 6:56pm. Last updated by Michael Levin May 4, 2018.
Looking for Jobs or Staff?
Check out the Codetown Jobs group.
InfoQ Reading List
OpenAI Begins Article Series on Codex CLI Internals

OpenAI recently published the first in a series of articles detailing the design and functionality of their Codex software development agent. The inaugural post highlights the internals of the Codex harness, the core component in the Codex CLI.
By Anthony AlfordEtleap Launches Iceberg Pipeline Platform to Simplify Enterprise Adoption of Apache Iceberg
Etleap has recently launched the Iceberg pipeline platform, a new managed data pipeline layer designed to let enterprises adopt Apache Iceberg without building or maintaining a complex custom stack.
By Craig RisiArticle: Working with Code Assistants: The Skeleton Architecture

Prevent AI-generated tech debt with Skeleton Architecture. This approach separates human-governed infrastructure (Skeleton) from AI-generated logic (Tissue) using Vertical Slices and Dependency Inversion. By enforcing security and flow control in rigid base classes, you constrain the AI to safe boundaries, enabling high velocity without compromising system integrity.
By Patrick FarryDev Proxy v2.1 Introduces Configuration Hot Reload and Stdio Traffic Proxying

The Dev Proxy team has released Dev Proxy version 2.1, introducing new features aimed at improving developer productivity and simplifying local testing workflows. This release focuses on faster iteration, better support for modern development tools, and several refinements across the proxy and its related tooling.
By Almir VukMongoDB Introduces Embedding and Reranking API on Atlas
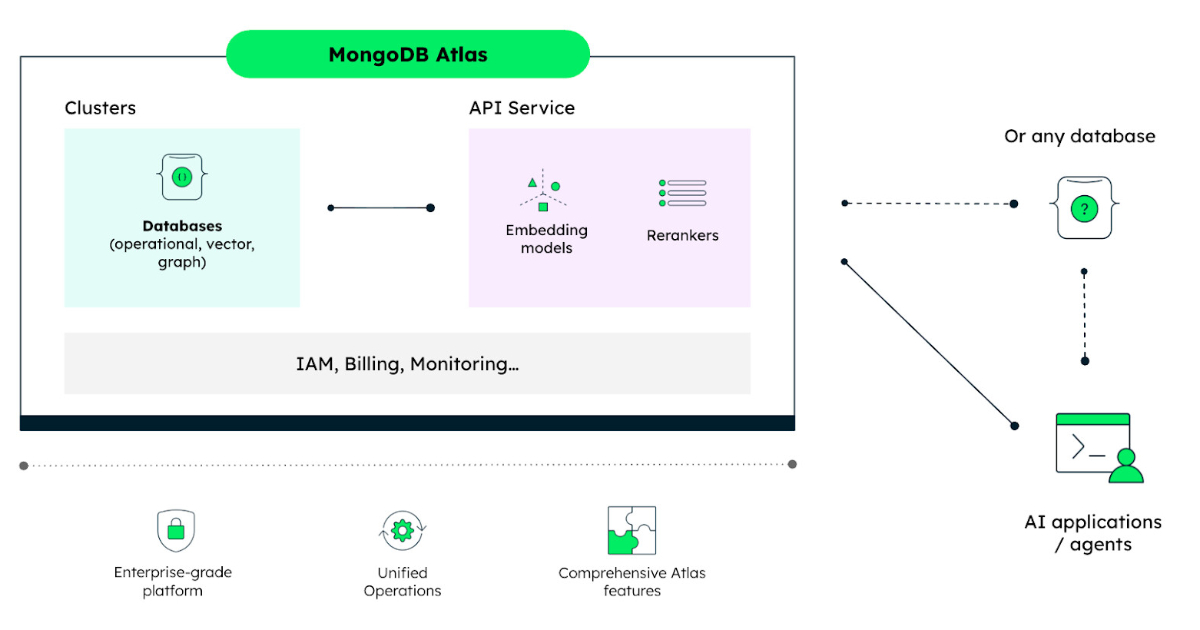
MongoDB has recently announced the public preview of its Embedding and Reranking API on MongoDB Atlas. The new API gives developers direct access to Voyage AI’s search models within the managed cloud database, enabling them to create features such as semantic search and AI-powered assistants within a single integrated environment, with consolidated monitoring and billing.
By Renato Losio
© 2026 Created by Michael Levin.
Powered by
![]()
Comment Wall (1 comment)
You need to be a member of Codetown to add comments!
Join Codetown